In our increasingly virtual-first world, delivering secure and verified virtual gatherings will be crucial, especially for the financial, medical, and legal industries. That’s why BeaconLive has partnered with Journey to deliver industry-first biometric authentication and advanced security ® for webinars, virtual events and continuing education.
Journey is a security industry pioneer and leader who has built an innovative zero knowledge identity network that solves security, privacy and customer experience simultaneously.
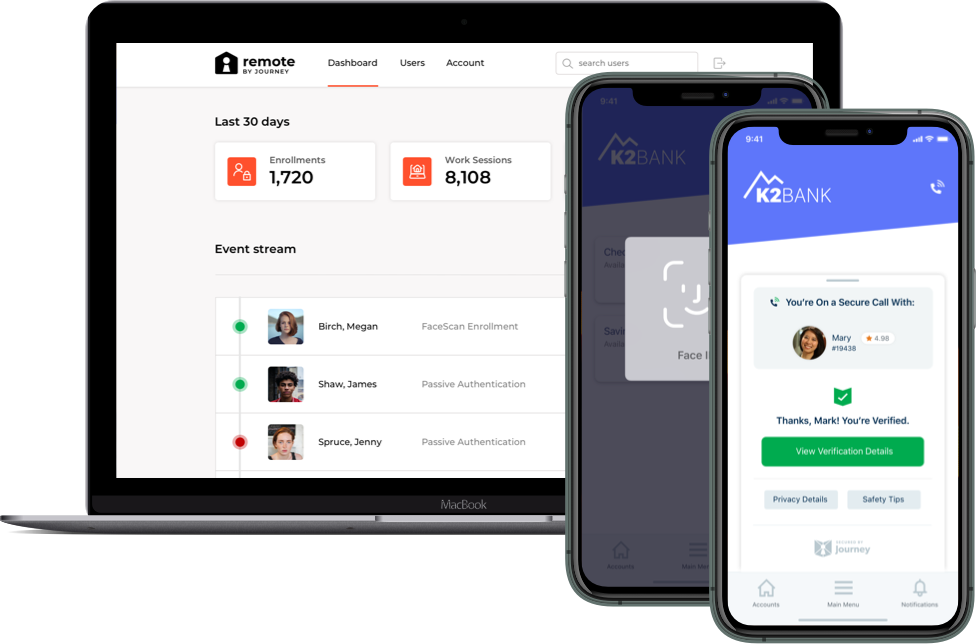
BeaconLive is the first and only platform in the industry to support verified identities in all virtual gatherings and content delivery. This will be especially crucial for webinar and video conferencing to protect the privacy of meetings and information, monetize proprietary content and establish verified voting.
Industry-standard encryption and security protocols have also been implemented to maintain privacy and security. These include:
-
Biometric authentication
-
GDPR compliance
-
ISO / IEC certificate
-
HIPAA compliance
-
CCPA Privacy Compliance
-
SOC2 / SSAE16 compliant data centers
-
PCI compliant payments
-
All media encrypted
Meetings and conferences that used to be considered not acceptable to hold virtually have now become acceptable, especially for the financial, legal, and medical industries, usually because there are few other viable options to physically getting together. These industries, like many others, are also seeing the vast benefits of gathering virtually. Technology and innovation is developing quickly to adhere to the security, privacy, and authentication concerns of professionals who require them.
Only with BeaconLive, you can enter your virtual conferences and events with confidence that your meeting data and information is secure and private. We will use biometric authentication - facial recognition, fingerprints, and/or voice prints - by utilizing the advanced sensors that are already built into today’s devices. As an event organizer, you can rest assured that your audience is who they say they are.
On average, individuals may have 200-300 identities on the internet as a culmination of all their logins, passwords, and user profiles. Verified trusted identity tools are utilizing not information that you may know (passwords, emails, or publicly accessible information about you), which hackers can steal, but something that you are (these are biometric - facial recognition, fingerprints, voice prints).
This security system is designed with privacy in mind, taking advantage of zero-knowledge systems to give our clients as much protection as possible. No downloads, plug-ins, or software installations are required.
Why Should Your Organization Care About Secure Online Gatherings and Learning Experiences?
Protect Against Fraud, Scammers, Hackers and Data Snatchers
There are many people out there who may be interested in hacking your data and online profiles. Hackers, scammers and data snatchers are looking to steal identities, bank account information, personal medical data and more and will do so by infiltrating your operating system. They can ambush their victims with deceptive URLs that lead to corrupted websites or secretly download malware / ransomware onto your computer.
If a hacker gets into your online meetings, they can easily put a link into the public chat or direct message other users on the virtual event / conference call with these corrupted URLs. They may also be able to use screen sharing capabilities and other interactive communication features to gain access to other users’ computers.
It is extremely important that any virtual event organizer utilizes a platform that has security and privacy measures put in place to:
-
Keep out hackers and scammers from entering the meeting
-
Monitor chat channels and suspicious user behaviors to quickly remove unwanted users from the meetings
Know Who Is Actually On Your Conference Call
For large-scale conference calls and meetings, or when users are easily able to turn off their video due to “low bandwidth,” sometimes it may be a concern of knowing who is actually on the other side of that virtual gathering. As recently reported by The New York Times, the co-founder of Ozy Media impersonated a YouTube executive on a call with Goldman Sachs, allegedly to influence a potential $40M investment.
Especially when it comes to shareholder meetings or board meetings, it is pertinent to verify the identity of key stakeholders. Or when it comes to establishing customer identity, you will want to ensure that the end-user is someone who you are actually trying to sell your product or service to. Thankfully, many of these issues are solvable and are being solved and more sophisticated mechanisms for joining meetings are being introduced to make it harder for someone to be in a meeting where they don’t belong. Enabling biometric authentication for verified identities in video and audio conferencing is critical to upholding business.
Eliminate ‘Zoombombing’
According to Wikipedia, ‘zoombombing’ or ‘zoom raiding’ refers to the unwanted, disruptive intrusion, generally by internet trolls, into a video conference call. In a typical Zoombombing incident, a teleconference session is hijacked by the insertion of material that is lewd, obscene, racist, misogynistic, homophobic, islamophobic or antisemetic in nature.
This problem is of such prominence that the FBI has put regulations into place and advises users of teleconferencing software to keep meetings private, require passwords or other forms of access control such as waiting rooms and limiting screen sharing access.
This is an obvious problem for companies and organizations who are seeking to conduct important and private business matters virtually. By enabling biometric authentication requirements to enter these meetings, you can ensure virtual conferences and meetings that won’t be disrupted.
Establish Trusted, Verified Online Communications For Your Brand
This integration Between BeaconLive and Journey creates a modern, user-friendly experience and only takes the user a few seconds to enroll in. The process is easy to integrate with existing tools and processes and is scalable if security is needed for large, sensitive calls.
Becoming the victim of a hacked or infiltrated meeting can harm your brand and the reputation of the participants, even if it is far from your organization's fault. However, as hackers and scammers continue to get more sophisticated in their ability to infiltrate their victims, so too does technology develop to protect against it. Ensure that your organization is delivering quality, private meetings and content online by partnering with a platform that has your security interests as the top of their agenda.
How Do I Implement Biometric Authentication & Advanced Security for My Virtual Events, Webinars and Continuing Education?
With BeaconLive, advanced security and biometric authentication for your virtual events, webinars and continuing education is made easy. With this new integration, you can authenticate attendees before, during and after events to make sure that the person consuming your proprietary content, voting in polls and participating in conversations is who they say they are.
Your BeaconLive account manager and event producer can help you implement this integration for advanced security and authentication. Feel free to contact us with any questions - our team is looking forward to launching your organization into this new realm of online events and content delivery.
Ensure secure and private online conferences, virtual events, webinars, and content delivery with BeaconLive. Our completely configurable, white-label platform can facilitate multiple tracks and breakout rooms, live to OnDemand content, closed captioning, eCommerce, roundtable networking and over 150 interactive features. We combine our virtual events platform with our proprietary Learning Management System to seamlessly incorporate Continuing Education, Corporate Compliance and Certificates into any virtual experience. Our event service experts act as an extension to your team, providing you with a tailored solution and professionally executed virtual experience. Learn more about our platform here.
